
Forensic investigation has confirmed the usage of Paragon’s Graphite spy ware platform in zero-click assaults that focused Apple iOS gadgets of at the very least two journalists in Europe.
Researchers at Citizen Lab say that the victims have been a outstanding European journalists who requested anonimity and Ciro Pellegrino, a journalist at Italian publication Fanpage.it.
“Our evaluation finds forensic proof confirming with excessive confidence that each a outstanding European journalist (who requests anonymity), and Italian journalist Ciro Pellegrino, have been focused with Paragon’s Graphite mercenary spy ware,” reviews Citizen Lab.
The assaults occurred in early 2025, and Apple despatched a notification to the 2 victims on April 29 informing that they’d been focused by “superior spy ware.”
The menace actor used Paragon’s Graphite spy ware platform to focus on the victims’ iPhone gadgets working iOS 18.2.1 and exploit CVE-2025-43200, which was a zero-day vulnerability on the time.
Apple describes the flaw as “a logic problem that existed when processing a maliciously crafted photograph or video shared through an iCloud Hyperlink.”
The seller addressed the vulnerability within the subsequent iOS launch, 18.3.1, on February 10, by including improved checks. Nevertheless, the CVE identifier was added earlier at this time to the safety bulletin .
BleepingComputer has reached out to Apple to make clear the date of fixing the vulnerability however haven’t acquired a response at publishing time.
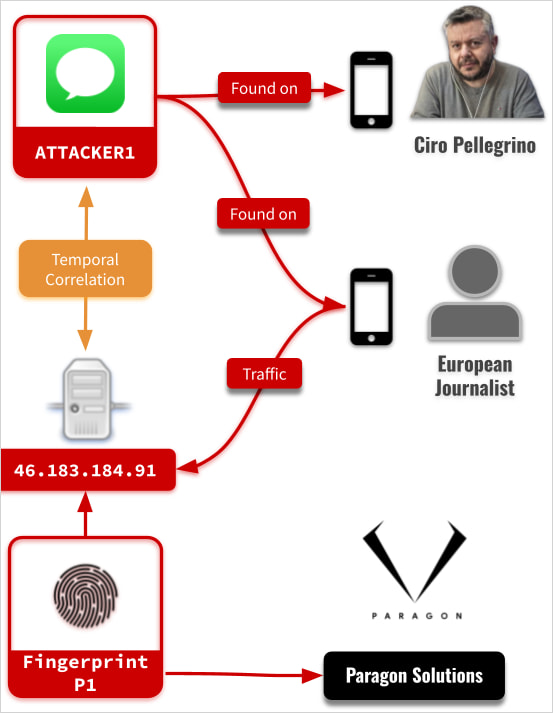
Based on Citizen Lab’s evaluation, Graphite’s supply vector was iMessage. The attacker used an account, generically labeled ‘ATTACKER1’ within the analysis, to ship specifically crafted messages that exploited CVE-2025-43200 for distant code execution.
This achieved the supply of the spy ware with none interplay from the goal, in what is known as a zero-click assault, and with out producing any seen indicators to alert the sufferer.
As soon as lively, the spy ware contacts a command-and-control (C2) server to obtain additional directions. Within the case confirmed by Citizen Lab, the contaminated cellphone related to https://46.183.184[.]91, a VPS linked to Paragon’s infrastructure.
This IP handle was hosted on EDIS International and was lively at the very least till April 12.
Supply: CitizenLabs
Though little hint was left on the gadgets, Citizen Lab was capable of get well some logs that contained sufficient proof to attribute the assaults to Paragon’s Graphite spy ware with excessive confidence.
The identical spy ware household was “caught” earlier this yr in one other zero-click assault exploiting a zero-day vulnerability in WhatsApp that focused different Italian victims.
Italian authorities have confirmed earlier this month a number of assaults towards people within the nation, together with journalist Francesco Cancellato and activists Luca Casarini and Dr. Giuseppe “Beppe” Caccia. Nevertheless, the events accountable for these assaults will not be publicly identified at the moment.
Patching used to imply advanced scripts, lengthy hours, and infinite fireplace drills. Not anymore.
On this new information, Tines breaks down how fashionable IT orgs are leveling up with automation. Patch sooner, cut back overhead, and give attention to strategic work — no advanced scripts required.





