
A big-scale malware marketing campaign particularly targets Minecraft gamers with malicious mods and cheats that infect Home windows units with infostealers that steal credentials, authentication tokens, and cryptocurrency wallets.
The marketing campaign, found by Test Level Analysis, is performed by the Stargazers Ghost Community and leverages the Minecraft huge modding ecosystem and legit companies like GitHub to succeed in a big viewers of potential targets.
Test Level has seen 1000’s of views, or hits, on Pastebin hyperlinks utilized by the risk actors to ship payloads to targets’ units, indicating the broad attain of this marketing campaign.
Stealthy Minecraft malware
The Stargazers Ghost Community is a distribution-as-a-service (DaaS) operation lively on GitHub since final yr, first documented by Test Level in a marketing campaign involving 3,000 accounts spreading infostealers.
The identical operation, which is boosted by faux GitHub stars, was noticed infecting over 17,000 methods in late 2024 with a novel Godot-based malware.
The most recent marketing campaign described by Test Level researchers Jaromír Hořejší and Antonis Terefos targets Minecraft with Java malware that evades detection by all anti-virus engines.
The researchers discovered a number of GitHub repositories run by Stargazers, disguised as Minecraft mods and cheats like Skyblock Extras, Polar Shopper, FunnyMap, Oringo, and Taunahi.
“We have now recognized roughly 500 GitHub repositories, together with these which might be forked or copied, which have been a part of this operation aimed toward Minecraft gamers,” Antonis Terefos informed BleepingComputer.
“We have additionally seen 700 stars produced by roughly 70 accounts.”
Supply: Test Level
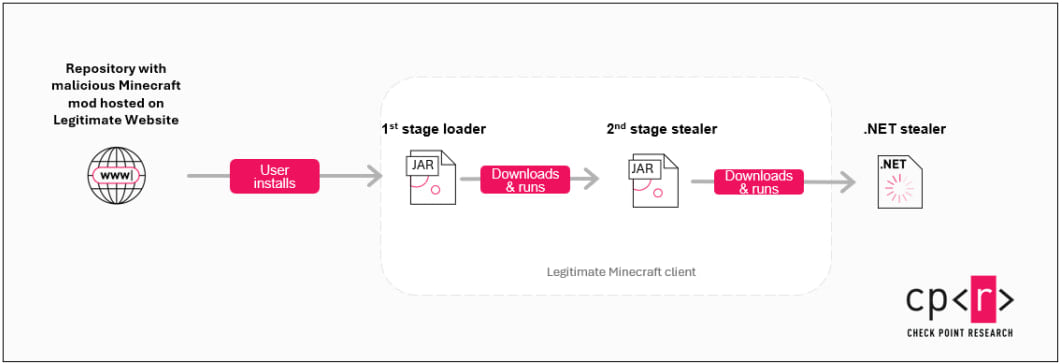
As soon as executed inside Minecraft, the first-stage JAR loader downloads the subsequent stage from Pastebin utilizing a base64 encoded URL, fetching a Java-based stealer.
This stealer targets Minecraft account tokens and consumer knowledge from the Minecraft launcher and well-liked third-party launchers like Feather, Lunar, and Important.
It additionally makes an attempt to steal Discord and Telegram account tokens, sending the stolen knowledge through HTTP POST requests to the attacker’s server.
The Java stealer additionally serves as a loader for the subsequent stage, a .NET-based stealer known as ’44 CALIBER,’ which is a extra “conventional” data stealer, making an attempt to grab data saved in internet browsers, VPN account knowledge, cryptocurrency wallets, Steam, Discord, and different apps.
Supply: Test Level
44 CALIBER additionally collects system data and clipboard knowledge and might seize screenshots of the sufferer’s laptop.
“After deobfuscation we will observe that it steals varied credentials from browsers (Chromium, Edge, Firefox), information (Desktop, Paperwork, %USERPROFILE%/Supply), Cryptocurrency wallets (Armory, AtomicWallet, BitcoinCore, Bytecoin, DashCore, Electrum, Ethereum, LitecoinCore, Monero, Exodus, Zcash, Jaxx), VPNs (ProtonVPN, OpenVPN, NordVPN), Steam, Discord, FileZilla, Telegram,” warns the researchers.
The stolen knowledge is exfiltrated through Discord webhooks, accompanied by Russian feedback. This clue, mixed with UTC+3 commit timestamps, means that the operators of this marketing campaign are Russian.
Test Level has shared the total indicators of compromise (IoCs) on the backside of its report to assist detect and block the risk.
To remain protected towards this and comparable campaigns, Microsoft gamers ought to solely obtain mods from respected platforms and verified neighborhood portals and follow trusted publishers.
If prompted to obtain from GitHub, verify the variety of begins, forks, and contributors, scrutinize commits for indicators of pretend exercise, and verify latest actions on the repository.
In the end, it’s prudent to make use of a separate “burner” Minecraft account when testing mods and keep away from logging into your primary account.





